Optimization vs. encryption
In article 11, we explained that the secret cryptographic key was encoded in the QR code, then scanned by the mobile device, and used by that device to encrypt data before upload.
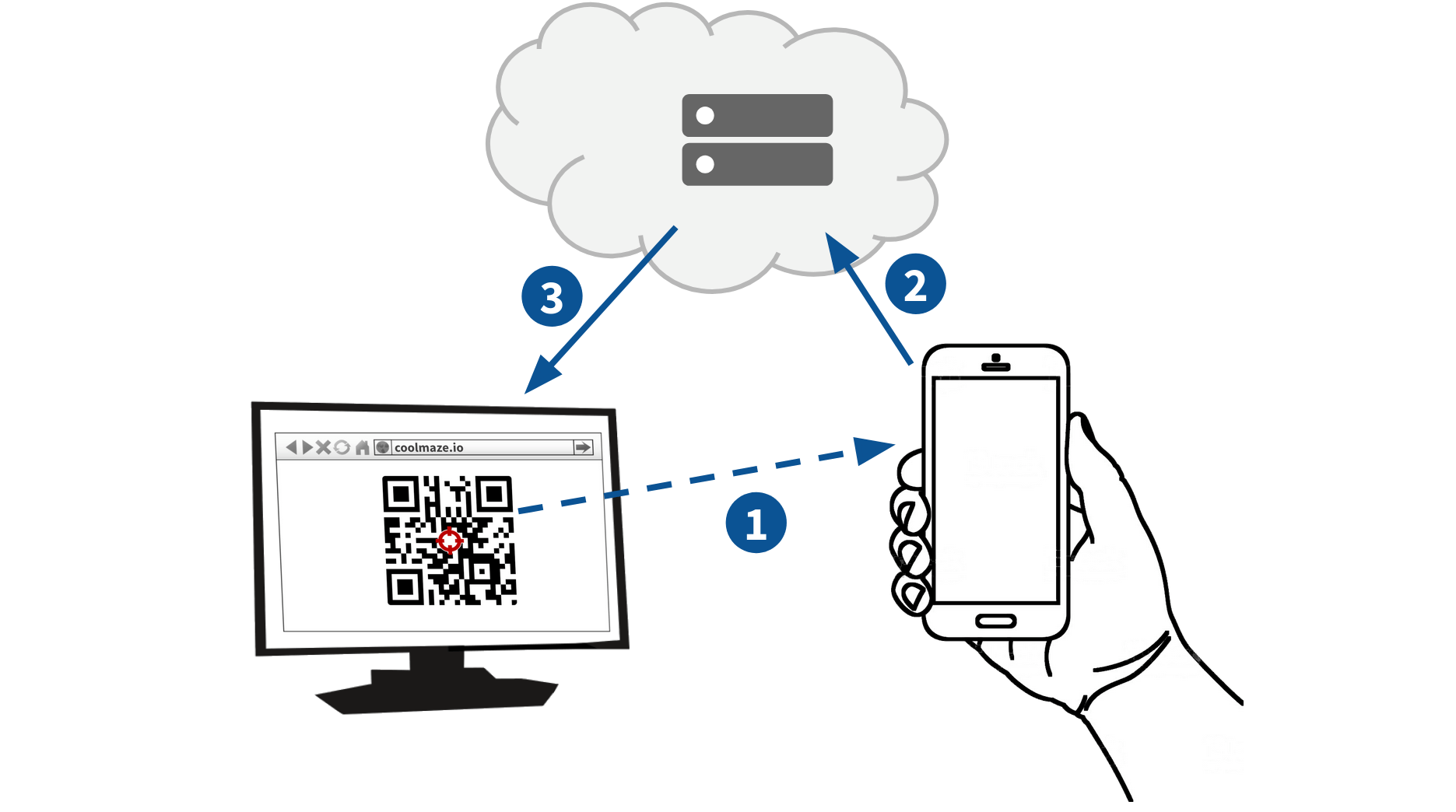
However, in article 7, we saw how the mobile device uploads the encrypted data before detecting the QR code. This strategy aims to boost performance and reduce total latency.
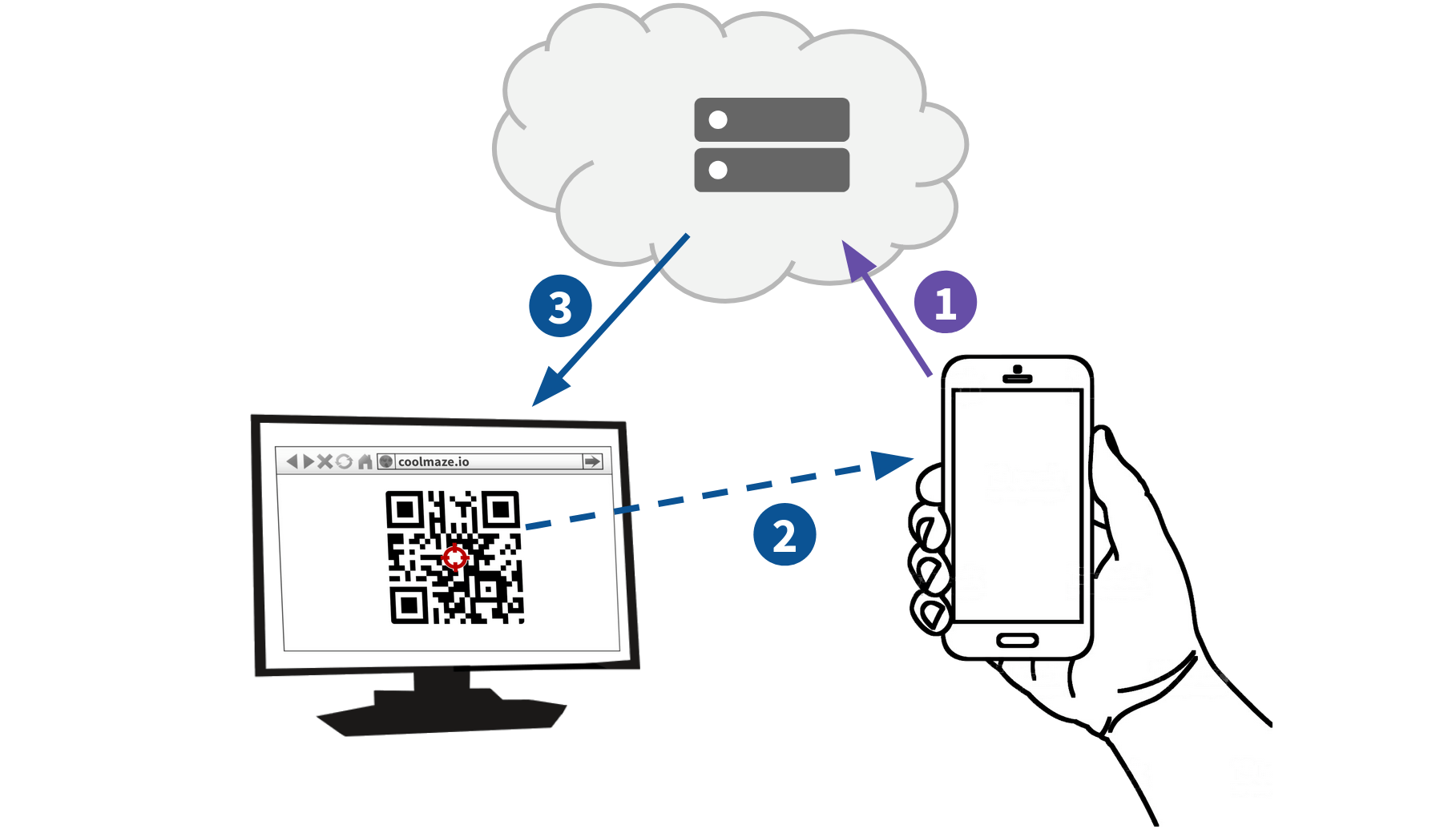
There’s a fundamental contradiction here. How can the mobile device encrypt and upload the data, before it even knows the secret encryption key?
The two-key solution
The solution lies in employing two secret keys: one “green” key and one “white” key. The mobile device first generates its own green key, immediately encrypts the user data, and uploads it to the server. Subsequently, it scans the QR code to read the “white” key generated by the target webpage, along with the routing ID. The encrypted data is now ready for delivery to the target, and the white key is already shared between the two ends of the communication.
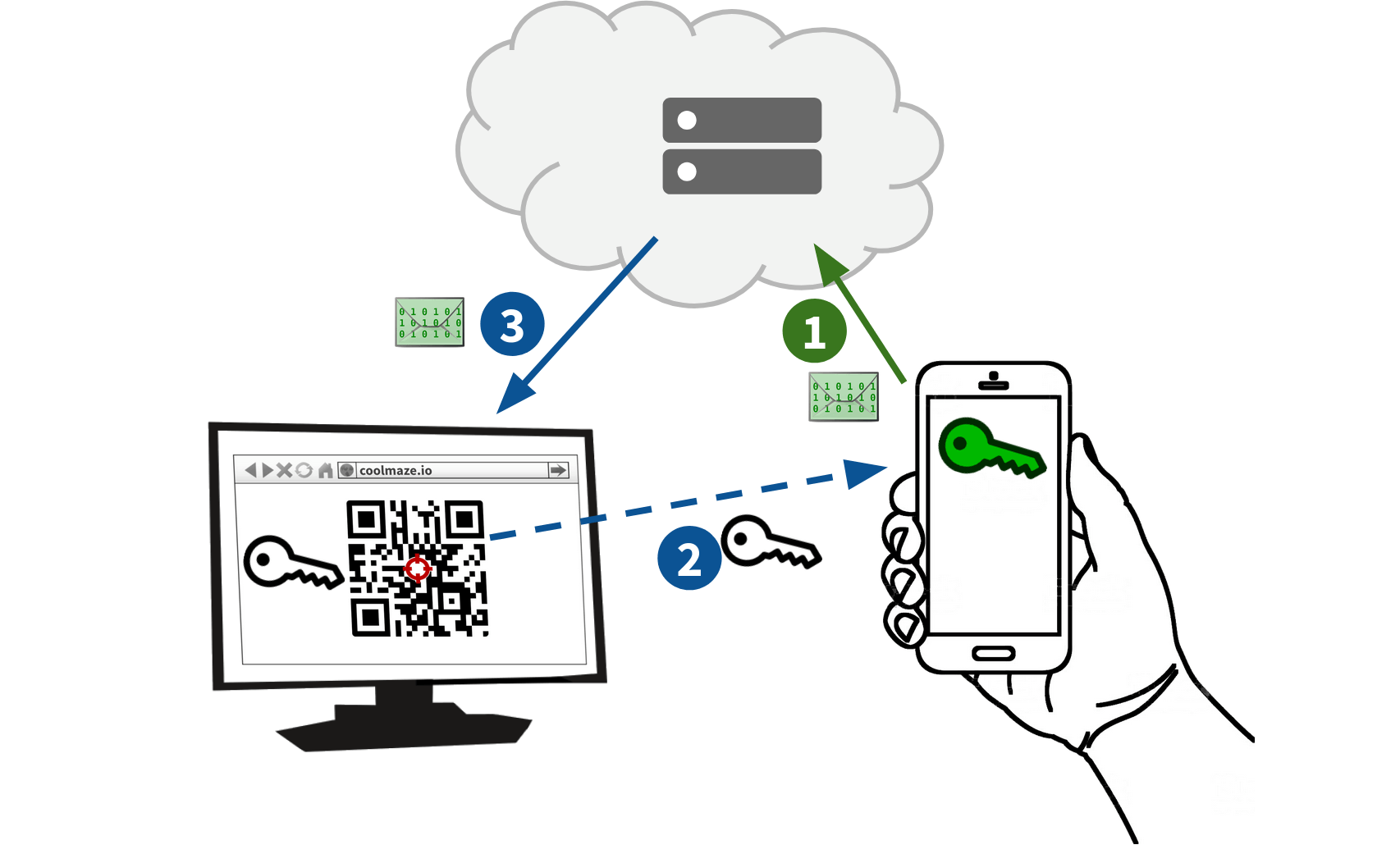
One last piece of the puzzle remains: We need to provide the green key to the target webpage, without exposing it to the server. To overcome this challenge, the mobile device encrypts the green key using the white key and sends it to the server for delivery to the target.
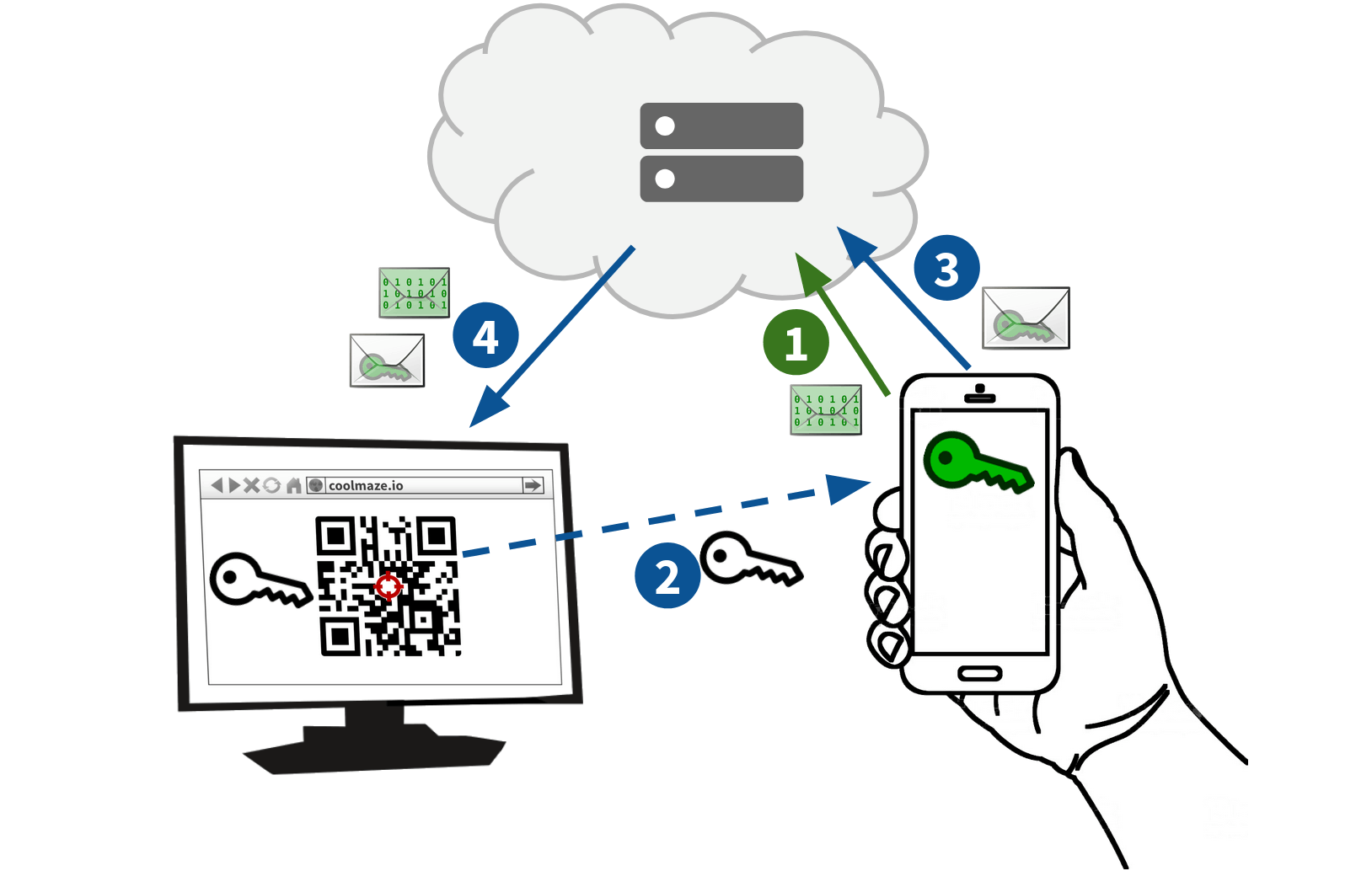
The target now possesses both the encrypted data and all the necessary secret keys. It uses its white key to decrypt the green key. It then uses the green key to decrypt the user data.
Encryption and decryption occur very quickly. Importantly, we ensure the plaintext value of the secret keys is never revealed to the server, preserving end-to-end encryption. By leveraging two keys, we maximize performance while fully protecting user privacy.